1. Introduction
On September 8, 2025, SwissBorg lost 192,600 SOL (~$41 million) when part of its Solana staking infrastructure, operated through Kiln, was compromised.
This wasn’t a smash-and-grab. Eight days earlier, on August 31, a transaction that looked like a routine unstake of 975 SOL quietly reassigned authority over multiple staking accounts to attacker-controlled addresses. From that moment, effective control of the wallets had been handed over to the attacker.
Eight days later, in just three minutes, the attacker drained everything.
2. SwissBorg and Kiln
SwissBorg is a Swiss wealth management app with more than $2 billion in assets under management, known for simplifying crypto investing through its Earn products.
For Solana Earn, SwissBorg outsourced part of its staking operations to Kiln, a professional validator operator. This is common practice: wealth and custody platforms usually rely on specialist operators whose sole focus is validator uptime, efficiency, and staking infrastructure.
But outsourcing shifts risk. Once Kiln’s API was compromised, SwissBorg’s users were directly exposed.
3. The Setup: Authority Delegation
To understand this attack, we first need to understand how authority delegation works on Solana.
On Solana, every stake account has two forms of authority:
Staker Authority: decides which validator the tokens are delegated to.
Withdrawer Authority: decides who can withdraw the funds.
These authorities can be reassigned as part of normal operations. For example, if you switch validators, you might transfer the staker authority.
The attacker exploited this flexibility.
Think of it like the fine print in a contract: what looked like an ordinary transaction reassigned withdrawer authority to the attacker, giving them the ability to move funds directly.
The result was an account takeover. As seen in the Bybit exploit, the attacker first seized control of the account itself, and only later moved the funds.
4. The Transaction
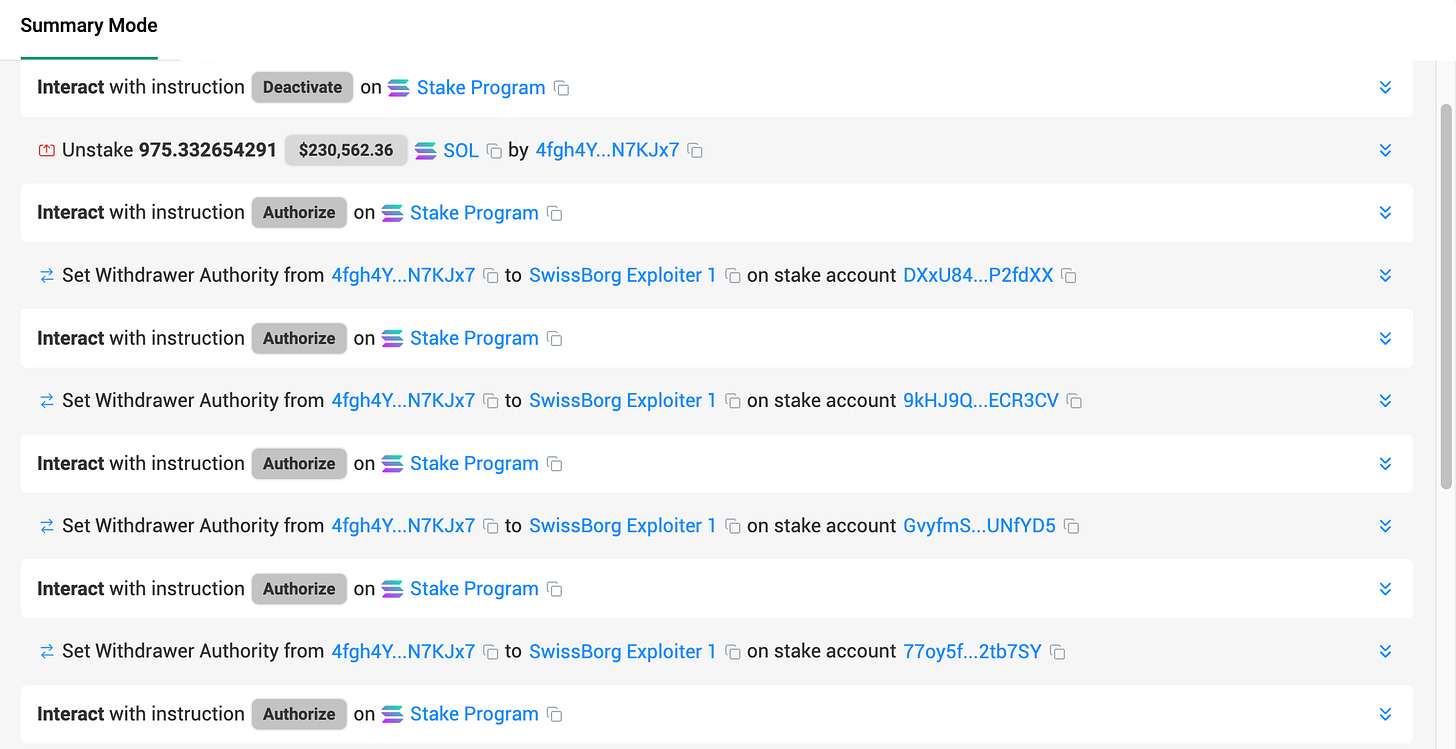
On August 31, 2025, Kiln executed what appeared to be a routine unstake of 975 SOL.
Hidden inside, however, were eight instructions that reassigned control of different stake accounts to an attacker-controlled address.
From that point forward, the attacker had on-chain authority. They no longer needed to rely on Kiln’s API, they could withdraw funds directly, bypassing any of the transaction policies that had been put in place.
5. The Blind Spot
Why wasn’t this caught?
Though not officially confirmed, the most likely explanation comes down to two factors:
Kiln’s API policies only validated withdrawals, checking whitelisted addresses and amounts and did not parse authority changes and/or
Blind signing allowed the transaction to slip through.
Blind signing is when a user or system approves a raw hexadecimal transaction without understanding its contents. On Solana, that might look like a long string such as 0x4f3cb2b… with no human-readable breakdown.
This should be decoded to make it human-readable, however there is always a risk it might be “blindly” approved by a human who “signs” without checking and realizing hidden authority changes were embedded. An API might auto-sign because authority instructions didn’t alter the destination of the unstake itself.
Either way, the result was the same: the transaction bypassed the checks in place, was signed, and instantly granted the attacker control of the stake accounts.
Analogy: It’s like approving a contract that you couldn’t read properly in order to process it quickly or a bank checking every wire transfer’s destination but ignoring the line where a new co-owner is added to the account.
There is also a more remote possibility that, similar to the Bybit exploit, the software decoding the raw transaction was manipulated to hide authority change instructions. However, no evidence or reporting has surfaced to suggest this occurred.
6. The Attack
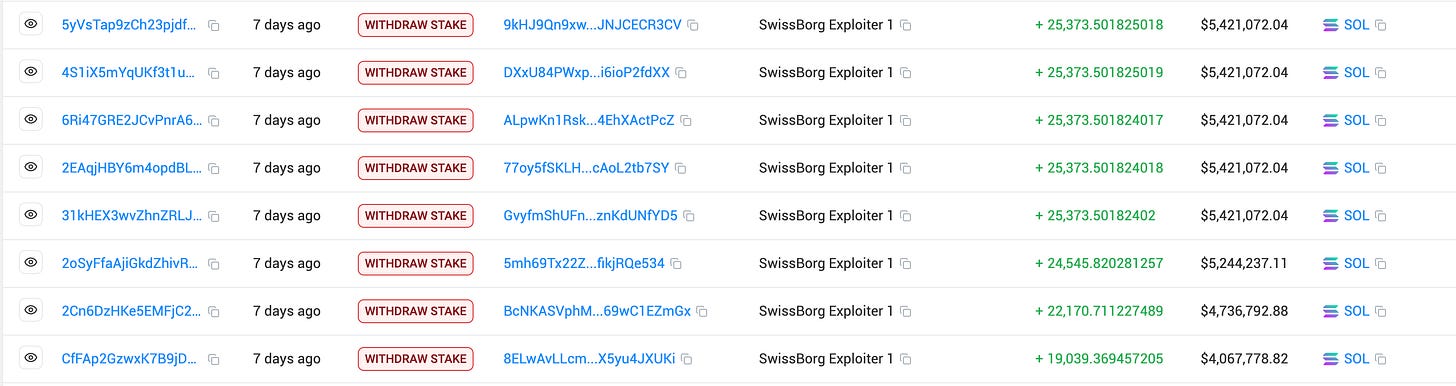
Eight days later, on September 8 at 12:02 UTC, the attacker executed.
Over three minutes and eight transactions, they drained 192,600 SOL (~$41.5M) from the compromised stake accounts into the attackers wallet.
7. The Aftermath
SwissBorg froze Solana Earn immediately and promised to reimburse all affected users. Kiln acknowledged the API breach, shut down affected services, and even exited its Ethereum validators as a precaution.
In the days following the theft:
189,524 SOL (now ~$44M) was transferred out to a single wallet and remains parked there.
3,000 SOL (~$0.6M) was transferred out via 3 transactions (here, here, here) and began multiple intermediate hops before being tested through exchanges, including a 100 SOL probe into Bitget.
Financially, the damage was containable. Reputationally, it was not. To customers, trust had been shaken in both SwissBorg and Kiln.
8. Why This Happened
Transaction policies by themselves are not enough. In this case, they failed to catch authority changes.
Once the attacker reassigned authorities, all other safeguards became irrelevant. Future filters may block this specific tactic, but attackers will always find new ways around static rules.
It isn’t just about where funds are going. It’s about who controls the account. When that shifted, silently, every transaction check could be bypassed.
9. The Last Line of Defense
The SwissBorg exploit shows why systems like Automatic Asset Extraction (AAE) are necessary. Human intervention cannot move at blockchain speed.
If defenders had been able to automatically detect anomalous authority changes, the Aug 31 transaction could have been blocked.
Automated defences like AAE don’t eliminate risk entirely, but they ensure that even when attackers find gaps in transaction policies, assets can still be rescued.
10. Conclusion
The SwissBorg / Kiln exploit shows how $41.5M can vanish in minutes, not because security was absent, but because there are always gaps policies can miss.
On August 31, authority over accounts was handed to the attacker. Eight days later, that control became a full drain. The pattern echoes other exploits like the Bybit hack: attackers don’t just drain accounts, they can take control first, then move the funds rapidly.
At that speed, humans cannot react. Only automated defenses can protect funds at blockchain speed. That’s why Circuit is pioneering Automatic Asset Extraction (AAE): a last line of defense that safeguards assets even when attackers weaponize normal operations into takeovers.
Harry Donnelly is the CEO & Founder of Circuit. Circuit protects against catastrophic digital asset losses, whether from hacks, stolen keys, or key mismanagement. Circuit is pioneering Automatic Asset Extraction (AAE) technology which enables you to instantly sweep assets to safety the moment a threat is detected, without altering your existing wallet infrastructure. Reach out to learn more.
Thanks to TJ Connolly for reviewing drafts of this piece and providing feedback.



Still missing the most important part: how was Kiln’s transaction crafting API response manipulated? Or wasn’t it and the unsigned transaction was modified on SB side?
At this point, given all Kiln apps and APIs are still down do you think they got their app and API software hacked -. Phishing or rogue employee?