How The $128m Balancer Exploit Happened
Breaking down the complexity of how rounding errors were used to steal $128m across 8 chains
1. Introduction
On November 3rd, 2025, $128 million vanished from Balancer across eight blockchains in under two hours.
In the immediate aftermath, explanations flooded in. An access control bug. A missing permission check. Something simple that had slipped through the cracks.
They were wrong.
What emerged was something far more sophisticated. Someone who understood Balancer’s mathematics, and how to exploit it.
The irony? Buried in Balancer’s code, right above the vulnerable function, sat a developer comment: “the impact of this rounding is expected to be minimal.”
They were wrong by $128 million.
This wasn’t bypassing security. This was finding the exact boundaries where precision breaks down, then exploiting those boundaries through calculated iteration, using maths as a weapon.
To understand how it happened, we need to start with what everyone got wrong.
2. How Balancer Works
Balancer is an automated market maker that has processed billions in volume since 2020.
Think of it like a bank vault holding multiple types of assets (ETH, stablecoins, wrapped Bitcoin etc) that users can swap between whenever they want.
When you deposit assets into a Balancer pool, you get a receipt token called BPT (Balancer Pool Token). If you own 1% of all BPT, you own 1% of everything in the vault. When you want your assets back, you return your BPT and withdraw your share.
The Price Calculation
Balancer always needs to be able to answer the question: what’s each BPT worth?
The price formula is simple:
BPT price = D / totalSupply
D is a mathematical constant called the invariant. This number must stay balanced across all swaps and satisfy the following formula (you don’t need to understand it):
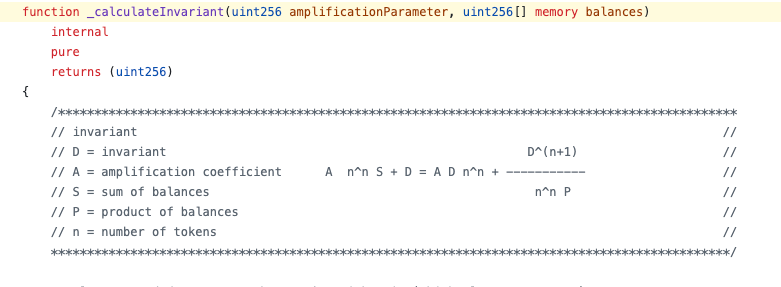
Think of D as a number representing the total value in the vault when everything is balanced.
The problem: if you manipulate D, then you can manipulate the price of the BPT tokens.
Example:
If D = $100 million and there are 100 million BPT tokens, each BPT is worth $1
If you make D drop to $90 million (while the vault still holds $100 million in real assets), each BPT gets priced at $0.90
You could buy BPT cheap, burn it for real assets, and pocket the difference
But how do you manipulate D?
The Decimal Problem
Calculating D requires a technical challenge: tokens have different decimal places. USDC has 6 decimals, Ethereum has 18, Wrapped Bitcoin has 8. Before Balancer can do any math, it needs everything in the same format.
The process Balancer follows:
Scale all tokens to 18 decimals (
_upscale()function)Calculate D using the scaled numbers (multiple division operations, each rounding down)
Use D to determine swap amounts
Scale results back to native decimals
The problem: the specific function _upscale() always rounds down. When calculating D, multiple rounding-down operations compound. Under normal conditions, these losses are negligible.
Because BPT price depends on D (BPT price = D / totalSupply), if you can deflate D through accumulated rounding errors, you deflate the price of BPT.
The developers knew. They documented this: “This is the only place where we round in the same direction for all amounts, as the impact of this rounding is expected to be minimal.”
For normal trading, they were right. But Balancer wasn’t built for just normal swaps.
Three Features That Became Weapons
Balancer was designed for capital efficiency through three features:
Composability: You can trade BPT within the pool itself. You can swap your receipt token for underlying assets in the same transaction, without actually withdrawing first.
Deferred Settlement: Multiple swaps in one transaction don’t settle until the end. You can have temporary negative balances as long as everything sums to zero by the end.
Flash Operations: By combining these two features, you can briefly use more liquidity than you actually own. Within a single transaction, it works almost like having a momentary loan, as long as everything balances out by the end.
These features made Balancer incredibly efficient for sophisticated users.
They also made it possible to manipulate the conditions under which D was calculated, and therefore manipulate BPT’s price.
3. The Attack
Links to Primary Attack Transaction here, Withdrawal Transaction here1
On November 3rd, 2025, someone executed one of the most mathematically sophisticated attacks in DeFi history.
The insight: those “minimal” rounding errors compound dramatically under specific conditions. The attacker discovered how to create those conditions.
Phase 1: Create the Conditions
Using Balancer’s three features in combination, the attacker drained pool liquidity to extreme lows.
They used Balancer’s ability to trade BPT inside the pool, combined with the fact that nothing settles until the end of a batch swap, to shuffle assets around in a way that pushed some token balances extremely low, all within a single transaction.
Balancer had safeguards: a minimum pool supply limit designed to prevent exactly this scenario. In practice, the combination of composable BPT and the rounding behavior let the attacker sidestep those protections and push certain balances to extreme lows.
Why Low Liquidity Matters
Consider what happens when Balancer’s code rounds down during calculations:
Example
With a pool holding 1,000,000 tokens, rounding down by 1 token = 0.0001% error. Negligible.
With a pool holding 10 tokens, rounding down by 1 token = 10% error. Catastrophic.
The rounding operation itself doesn’t change, it’s still rounding down by roughly the same absolute amount. But when the pool is nearly empty, that same rounding becomes a bigger percentage of the total.
This matters because D (the invariant) is calculated using the token balances in the pool. When those balances are small, every division operation in the calculation takes a larger percentage bite. The accumulated rounding errors cause D to be significantly underestimated.
Phase 2: Compound the Errors
With liquidity reduced, the attacker executed dozens of micro-swaps in alternating patterns, all within a single transaction.
Remember the swap process in section 2: scale up (rounding down), calculate D (multiple rounding-down operations), scale back (rounding down again). At normal liquidity, these losses are negligible.
At the reduced liquidity levels the attacker created, each iteration compounded the rounding errors as large percentage losses. Each new calculation of D used the deflated result from the previous iteration, building accumulated errors with every swap.
The attacker wasn’t guessing. They deployed a “math helper2” contract that searched for rounding boundaries, the exact token amounts where precision breaks down most severely, testing parameters to find the point of maximum exploitation.
Phase 3: Extract the Value
After dozens of iterations, D had been deflated significantly through accumulated rounding errors.
Going back to our formula: BPT price = D / totalSupply
With D artificially low, BPT was now dramatically undervalued. The attacker burned BPT to withdraw real assets. The pools calculated payouts based on the deflated D, giving them far more value than the BPT was worth.
Everything settled to zero at transaction end. Every swap was mathematically valid according to Balancer’s code. But the accumulated precision loss meant pools across multiple chains were drained of millions.
The Sophistication
This wasn’t discovered by accident. The attacker deployed custom smart contracts that executed the attack with precision, optimizing parameters to be able to extract as much value as possible. This required detailed understanding of StableSwap mathematics, Balancer’s rounding functions, and how to combine Balancer’s features atomically within a single transaction.
They deployed it across eight blockchains with the following results:
Ethereum: $99M
Berachain: $12.86M
Arbitrum: $6.86M
Base: $3.9M
Sonic: $3.44M
Optimism: $1.58M
Polygon: $232K
Same vulnerability everywhere. Same method. Two hours. $128 million total.
4. The Aftermath
The attack hit eight blockchains simultaneously. Same vulnerability, same method, different responses.
Every chain running Balancer V2 was vulnerable. 25+ protocols that had forked Balancer’s code inherited the same flaw. When Balancer broke, they all broke simultaneously.
The Whitehat Response
Not everyone was looting.
StakeWise executed emergency multisig calls, recovering $20.7M, roughly 73% of what was stolen from their pools. BitFinding bots intercepted $600K. Base MEV bots recovered $150K. Whitehats secured $4.1M from vulnerable pools before attackers could reach them.
Blockchain Response
Different chains made different choices about how to respond. Smaller chains went to extraordinary lengths to stop the attacker:
Ethereum: No changes. Transactions stood. Immutability over recovery. The original blockchain philosophy held firm even at $99M cost.
Berachain: Validators halted the entire chain. Executed an emergency hard fork. Rolled back the $12.86M theft completely.
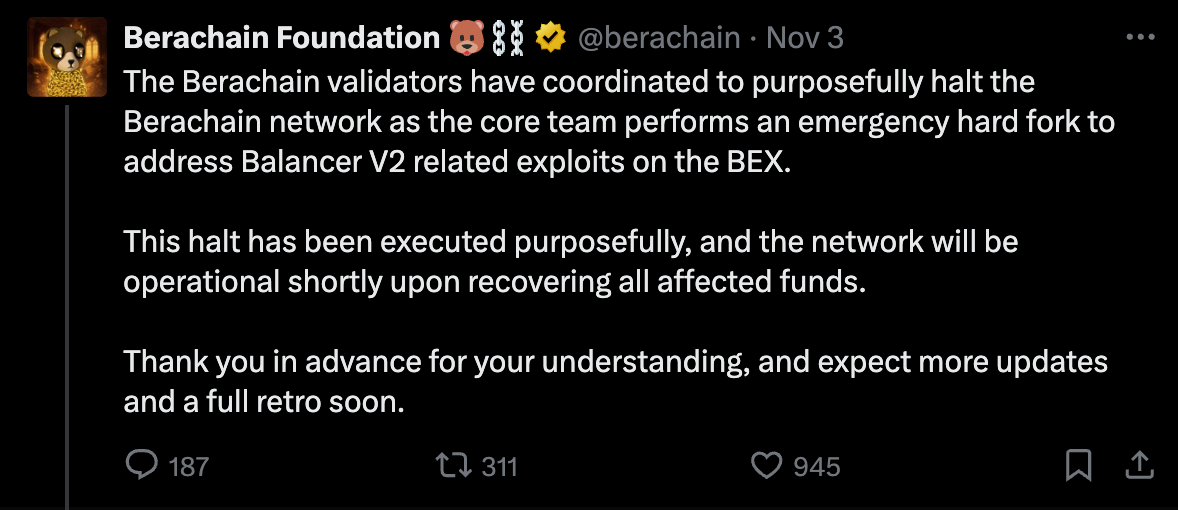
Sonic: Deployed emergency freeze functionality mid-attack. Zeroed out attacker addresses on-chain, preventing fund movement.
Polygon: Validators censored the attacker’s transactions. Coordinated to freeze stolen assets without code changes.
Gnosis: Restricted outbound bridge activity to trap funds before they could escape to other chains.
DeFi’s composability, the beauty of money Legos that allows protocols building on protocols, code forking code, amplifies both innovation and vulnerability. A single flaw doesn’t stay contained. When one Lego block breaks in DeFi, you discover how many towers were built on top of it.
5. Why Wasn’t It Discovered Earlier?
Balancer had elite security credentials: Trail of Bits, Certora, OpenZeppelin, ABDK. Over a dozen audits across four years. Billions in volume processed.
The gap: audits tested normal conditions. They didn’t test the adversarial rounding boundaries where precision breaks down under extreme low liquidity and repeated iteration.
6. Conclusion
This wasn’t a missing permission check or forgotten access control. This was mathematics weaponized at the boundaries where precision breaks down, by an attacker with incredible sophistication.
The Broader Pattern
DeFi’s composability amplifies both innovation and risk. When 25+ protocols fork the same code, they fork the same vulnerabilities. A flaw can hide for years, audited, battle-tested, processing billions in volume, then cascade across chains simultaneously once discovered.
Balancer had years of audits from elite firms. It didn’t matter. The code comment said impact “expected to be minimal.” For four years, it was. Until someone engineered the exact conditions where minimal became catastrophic.
Harry Donnelly is CEO & Founder of Circuit. Circuit’s platform protects against catastrophic digital asset losses and unlocks significant discounts on digital asset crime insurance from Lloyds of London underwriters. Reach out to learn more.
Credit to the great articles from Coinspect and Rekt below which I used to help gain a better picture of what happened during the exploit.
https://rekt.news/balancer-rekt2
https://www.coinspect.com/blog/balancer-rate-manipulation-exploit/